Table of Contents: Introduction to Workflows The Five Steps of Workflow 1. Initiation 2. Planning 3. Execution 4. Monitoring 5. Completion Types of Workflows Challenges in Implementing Workflows Conclusion FAQ Introduction to 5 Steps of Workflow? Did you realize a structured method can change how your business runs? Workflows are structured sequences of activities, decisions, […]
Table of Contents: Introduction to Workflow Stages The 8 Stages of Workflow Planning Designing the Process Assigning Roles and Setting Up Resources Executing the Work Monitoring Progress Analyzing Results Optimizing the Workflow Automation Benefits of Understanding Workflow Stages Adapting Workflow Stages Across Industries Conclusion FAQ Understanding Workflow Stages Are your projects constantly facing delays and […]
Securing Mobile Devices in the Enterprise: A Comprehensive Guide Key Takeaways Mobile devices are indispensable in modern workplaces but come with significant security challenges. Enterprises must balance productivity with robust security measures to protect sensitive data. Awareness of evolving threats and proactive security measures is critical for safeguarding enterprise networks. Introduction Mobile devices are integral […]
Risk Assessment: Escalation of Violence due to Rising Inflation in Nigeria I saw a video where what looks like security agents are fight with members of the public. The video came with this caption “In this economy you re going to collect revenue for the state you have to dig Yr grave first oooo. This […]
10 Must-Know Features of Azure Cloud Shell Azure Cloud Shell is a versatile tool for managing Azure resources, providing users with a command-line environment directly from their browser. Here are the top 10 features that make Azure Cloud Shell a powerful tool for cloud management: 1. Temporary Environment Azure Cloud Shell is temporary, meaning every […]
Decoding Google’s Ranking Algorithm: SEO Secrets Revealed (Maybe) Key Takeaway A leaked document, believed to be from Google, reveals insights into how Google ranks websites in search results. Content is king, but comprehensiveness, freshness, and title optimization are all important factors. Summary Content relevance, depth, and comprehensiveness: Google rewards websites that thoroughly address a topic. Content […]
Check Point Vulnerability CVE-2024-24919: A Deep Dive and Patch Reminder Key Takeaway Check Point Security Gateways with Remote Access VPN or Mobile Access enabled were vulnerable to a critical security flaw (CVE-2024-24919) that allowed attackers to steal sensitive information, potentially compromising the entire network. Summary Check Point security appliances marketed as highly secure were found […]
Microsoft Shuts Down Nigeria Development Center: A Missed Opportunity? Key Takeaway Microsoft is shutting down its Africa Development Centre in Lagos, Nigeria, which will lead to job losses. Summary Microsoft is closing its Africa Development Centre in Lagos, Nigeria. The center was opened in 2022 as part of Microsoft’s push to deliver high-end engineering and […]
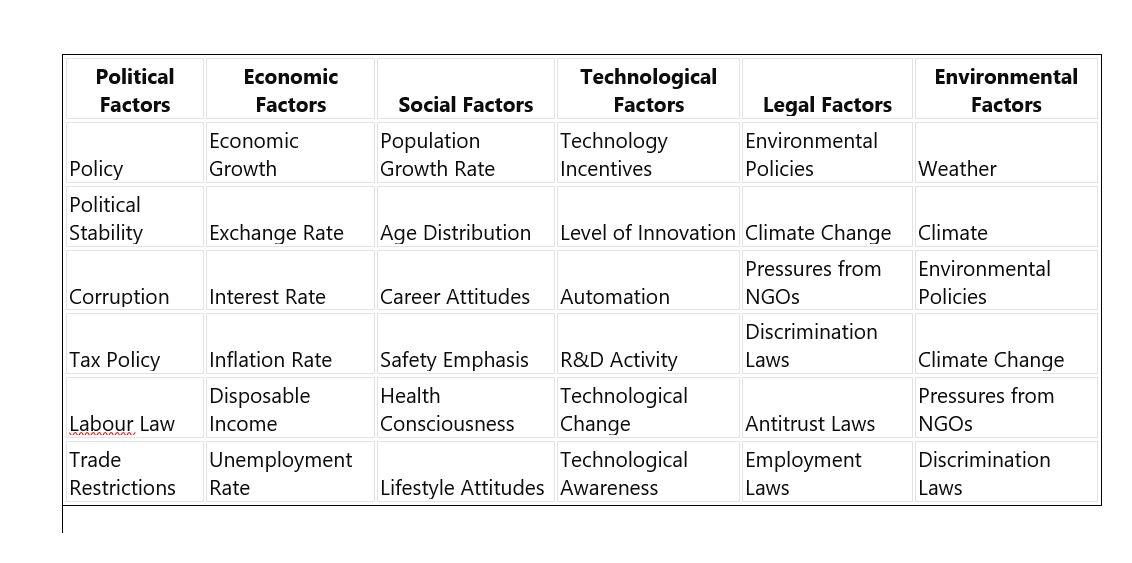
Effective Risk Management with PESTLE Technique 1. Introduction Construction projects are intricate endeavors, each with its own set of challenges and uncertainties. From skyscrapers to bridges, every project demands meticulous planning and execution. However, the construction industry is notorious for its susceptibility to risks. Factors like long gestation periods, substantial investments, and the non-tradability of […]
Table of Contents: What Exactly Is Corporate Governance? Why Does Corporate Governance Matter Globally? The Evolution of Corporate Governance Core Principles Across Borders Different Models Around The World Challenges Facing Global Corporate Governance The Future Outlook: Toward Integrated ESG Governance FAQ Corporate Governance: Shaping Ethical and Sustainable Business Practices Isn’t it time for companies to […]